As much as you'd love for your employees to only browse local files on the company server, the internet is far too tempting of a resource (or distraction) for them to ignore. In combination with the increase in movement to cloud based services, we are spending more time online than not.
In an online work environment, it is necessary to screen all incoming and outgoing connections to ensure they are in accordance with your cybersecurity plan. However, it is difficult to keep track of all browsing data at once, and cybercriminals are constantly devising new domain names not recognized as malicious by your firewall.
Here's a list of 5 common concerns businesses have when it comes to web security and some prevention tips from the pros to allay your woes.
1. Acceptable Use Violations
The internet can be a fantastic resource and a fantastic distractor for your work. What's to stop users from taking up office bandwidth to upload latest vacation pictures to Facebook or watching cat videos all day?
Solution: Employee monitoring software
Employee monitoring software allows employers to track browsing activity on your network in real time with an option to let employees know (or not) that you're watching. This can help increase productivity and catch breaches to acceptable use policies.
Keep in mind, web surfing is a normal office occurrence and companies shouldn't ban the idea of an employee checking Twitter. But from monitoring browsing statistics, businesses can see who is truly abusing the system and not utilizing their time efficiently.
2. Keeping Mobile Connections Secure
Internet of Things (IoT) devices and Bring Your Own Device (BYOD) policies have become the norm in many modern companies. Though these office trends can increase collaboration and efficiency in your office, they can also create a plethora of new access points for viruses and malware to enter your network.
If you've read our 3 Easy Steps for Email Security, you know that coworkers browsing personal emails through the company server can create malware entry points. The same can be said for browsing the web; simply visiting a malicious website can invite viruses in under the radar.
Solution: Cloud-based web content filter
To remedy this issue, we recommend signing up for a cloud-based web content filter. Unlike local content filters, a cloud-based one is able to track browsing content from all sites of your business in one place, including mobile employees. By checking the reputation of a website using DNS lookup, a web content filter can determine the trustworthiness of a site and allow or deny access.
3. Command & Control Malware
It's near impossible to keep your network completely clean. Inevitably, some cybercriminal will develop malware clever enough to bypass your perimeter and download onto a device in your network. However, the downloaded program itself is not comprehensive enough to encrypt your computer for a ransom or create a botnet. Instead, a compromised device must reach out to a command & control (C2) server to receive the next instructions on how to continue to wreak havoc.
If you can quarantine a device in your network before it can connect to a command & control server, you can prevent the malicious program from receiving its next set of instructions. Without the ability to connect to a C2 server, the computer virus will effectively remain "dormant" and not be able to execute malicious commands.
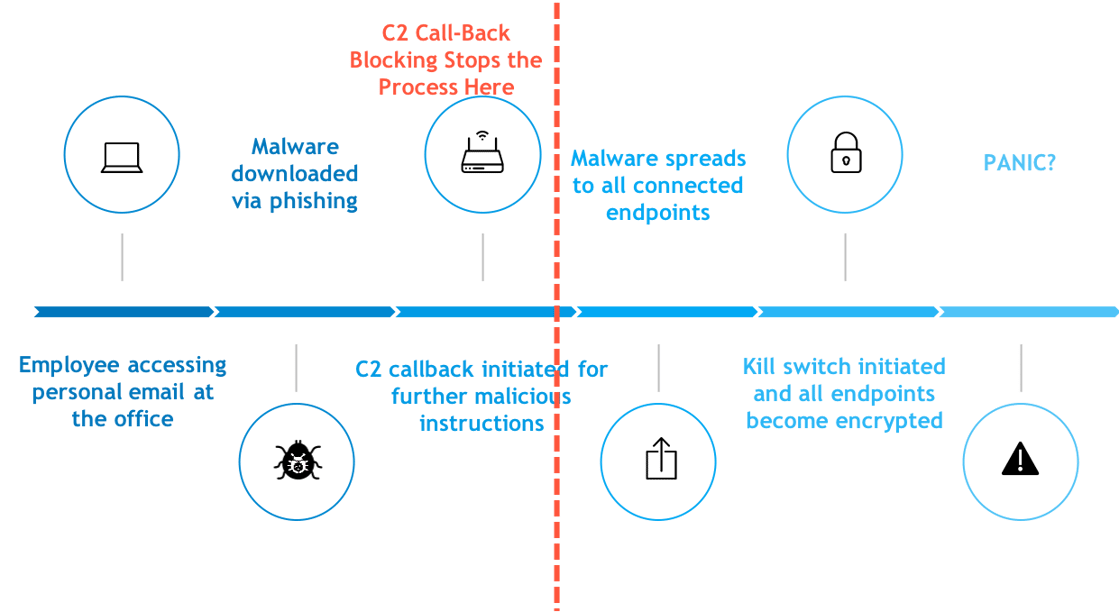
This is a great technique for preventing malware from spreading and executing, but unfortunately, using a traditional firewall-based security approach, this type of remediation is only available for on-site office networks. Once again, the proliferation of mobile employees has created the need for a wider security shield.
Solution: Blocking C2 Traffic at the Device Level
To prevent command & control malware from compromising your off-net users, you must have a security solution that extends beyond the on-site network. In addition, your solution should have a quarantine function to disconnect an infected endpoint from the rest of your network. Though the malware you downloaded is unable to establish connections outside of your network, it can still spread to all devices. The combination of a quarantine function and C2 call-back blocking creates a much stronger layer of security that can effectively combat malware.
4. DNS Lookup Slowing Down your Network
When you browse the web, your computer reaches out to other networks, which must then approve the connection for you to access the site. Each machine and network has its own IP address, which is used by other devices on the internet to identify the machine you are using as a unique connection.
Just like the contacts app on your phone, IP addresses are stored in an internet phone book called the Domain Name System or DNS. When a company has many users all going through the above process to make a website connection request, it can really slow down your network.
Solution: Content filter with built-in DNS lookup
We recommend, not removing any security protocol, but getting a cloud-based content filter that has DNS lookup built-in. Instead of having to request your ISP for a DNS lookup, these cloud-based filters will immediately check if a domain is malicious or not and only quarantine a device if a connection is considered risky.
5. Time and cost of managing web security
Finally, having to purchase an employee monitoring software, a web content filter with DNS lookup built-in, and C2 callback blocking can become a costly investment.
Solution: All-in-one cloud-based security service
Architected by Tekscape, Arma is an end-to end managed security solution designed to protect your business beyond the network perimeters. Integrating components of Cisco's leading portfolio, Arma is a scalable solution that protects your organization throughout the entire attack continuum. A Security-as-a-service solution like Arma can encompass the capabilities of employee monitoring software, cloud-based web content filter, and utilize products like TALOS, Cisco's worldwide database of domains for DNS lookups.
In addition to security bundles that answer all your woes, there is the option for managed services to take care of everything so you don't have to, which leaves you free to focus on growing your company.
 Download Brief: Advanced Malware Protection foe Endpoints and Cisco Umbrella Overview
Download Brief: Advanced Malware Protection foe Endpoints and Cisco Umbrella Overview
An estimated 70% of breaches start on endpoints - laptops, workstations, servers, and mobile devices. Why do endpoints continue to be the primary point of entry for attacks?
What's next? Download the solution brief and know more about Advanced Malware Protection and Cisco Umbrella, two rock-star solutions to help you protect your endpoints.





